Pen-Testing as a Service
Build up your cyber resilience
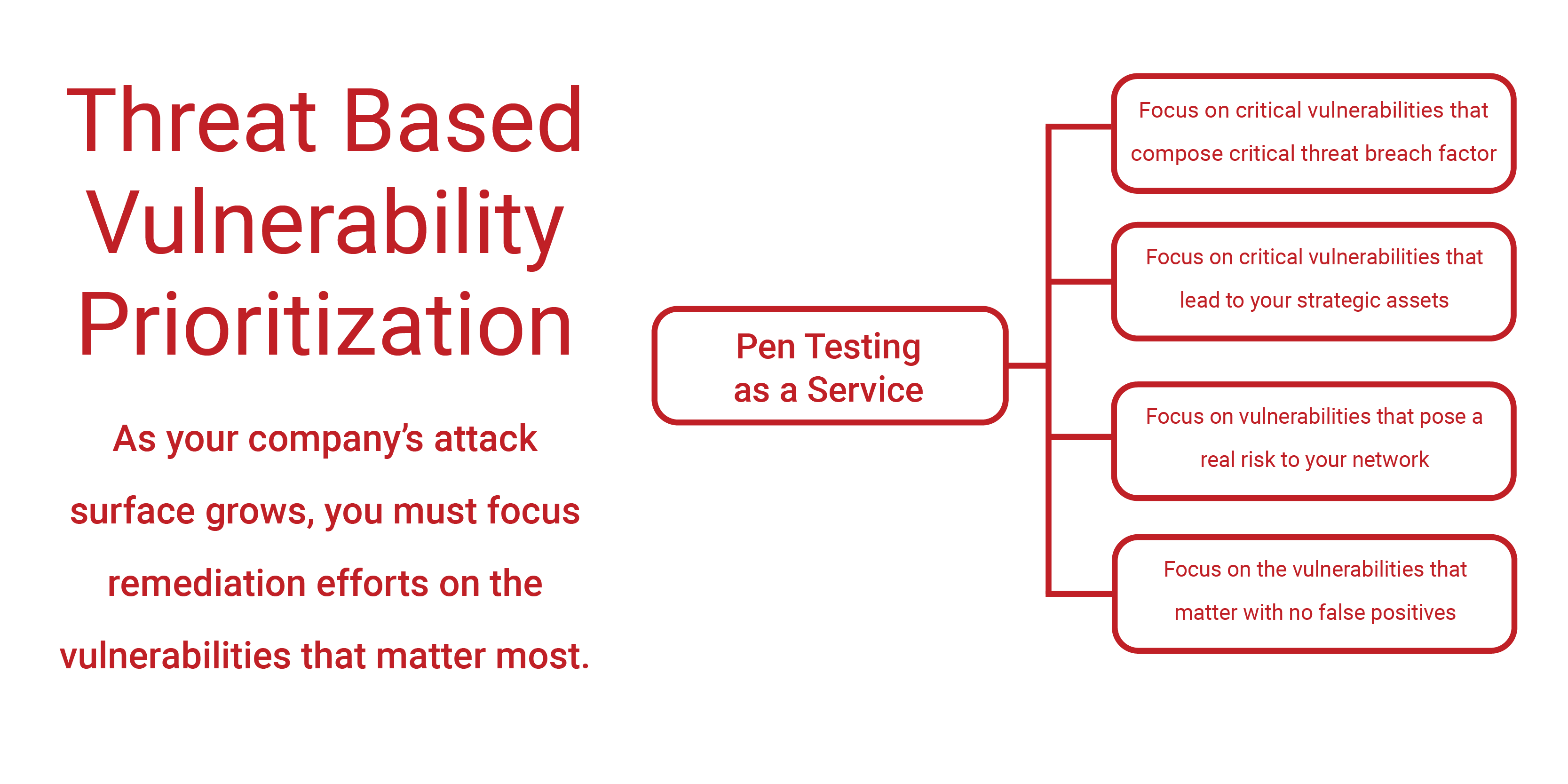
AGT Networks Pen-Testing as a Service continuously conducts ethical exploits on infrastructure vulnerabilities. Our Pen-testing platform alerts you to prioritized threat-based weaknesses based on real pen-testing discoveries.
Protect Your Reputation
The risk of being hacked is greater than ever, and your company’s reputation is at risk. Traditional methods such as anti-virus software and firewalls are no longer enough. As networks, users, devices, and applications constantly change and expose vulnerabilities, it is critical to pen-test frequently. Pen-Testing as a Service assures you can validate your cybersecurity posture daily to keep your guard up and eliminate potential threats.
The Cybersecurity Challenge
As hackers become more sophisticated, corporate security officers must learn to integrate the hacker’s perspective into their ongoing cyber defense strategy. Penetration testing has traditionally been completed manually by service firms, deploying expensive labor to uncover hidden vulnerabilities and produce lengthy reports, with little transparency along the way.
Continuous Protection
It is critical to consistently check your security controls and defenses across your organizational networks. AGT Networks Pen Test as a Service continuously tests your entire infrastructure with a wide array of hacking techniques ensuring that you remain resilient regardless of how the hacker is trying to break in.
How does PTaaS Work?
PTaaS Benefits
Agentless
Zero installations or network configurations
Automatic
Worry-free automatic pen-test process
Exploits
Harmless exploits without service interruption
Execution
Re-test and validate corrective actions across your organization.
Attack Visibility
See every step in the attack vector to understand the hacker's perspective.
Prioritized Remediation
Get a clear summary of the critical remediation steps to perform.
Latest Hacking Tech
Pen testing techniques are the most current
24/7
Pen-Tests
Run pen-tests every day, week or whenever needed.
Test as frequently as needed (daily, weekly or monthly). Because networks, users, devices and applications constantly change and expose vulnerabilities, it is critical to pen-test continually.
Malicious hackers constantly evolve their techniques and tools; therefore, it is critical that your risk validation tools evolve as fast as the hackers. assures that you match and evolve the depth of “off the books” pen-testing techniques.
PTaaS is a proactive solution for identifying the biggest areas of weakness in your IT systems and for preventing your business from serious financial and reputational losses.
Focused on the inside threat, mimics the hacker’s attack - automating the discovery of vulnerabilities and performing ethical exploits, while ensuring an undisrupted network operation. Detailed reports are produced together with proposed remediations, one step ahead of tomorrow’s malicious hacker.
PTaaS can help you comply with security regulations dictated by the leading security standards, such as PCI, HIPAA and ISO 27001, and avoid the heavy fines associated with non-compliance.
PTaaS can help you avoid costly security breaches that put your organization’s reputation and customers’ loyalty at stake.
If you are interested in learning more about PTaaS please contact us using the button below.